0day Exploit Database 🌴 on Twitter: "Do you want to buy or sell exploits? #1337day #Exploit #0day Market. green vs black style. http://t.co/Di2f0b8Qz9 http://t.co/pNKifjogn6" / Twitter
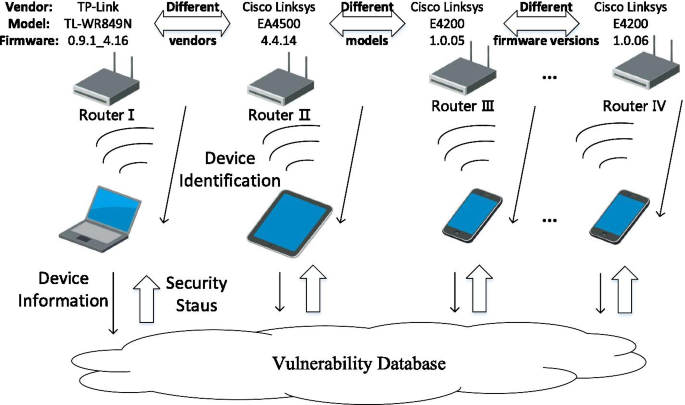
WNV-Detector: automated and scalable detection of wireless network vulnerabilities | EURASIP Journal on Wireless Communications and Networking | Full Text

Advisory: Cisco Small Business RV Series Routers Web Filter Database Update Command Injection Vulnerability - ONEKEY
Freshly Disclosed Vulnerability CVE-2021-20090 Exploited in the Wild | Official Juniper Networks Blogs