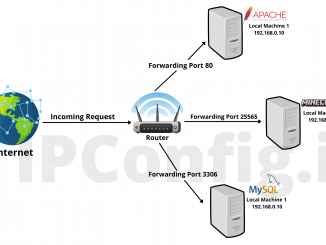
Hmwk-PA1-FW-DMZ.docx - Name: Tobi Bakare This assignment is to be done individually. Due date for this assignment is in LEARN. Refer to the | Course Hero
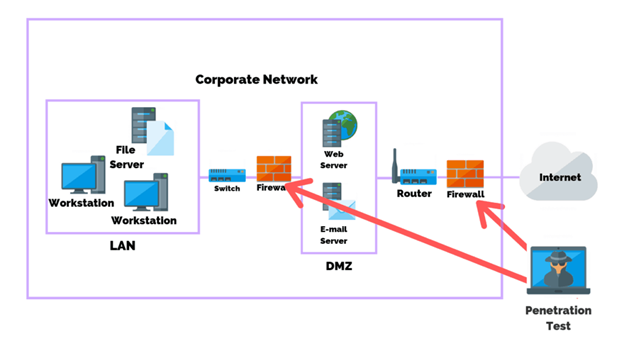
What is WAN, LAN, and DMZ? How does it relate to a firewall setup? I'm learning about firewalls, and I'm confused on this. - Quora
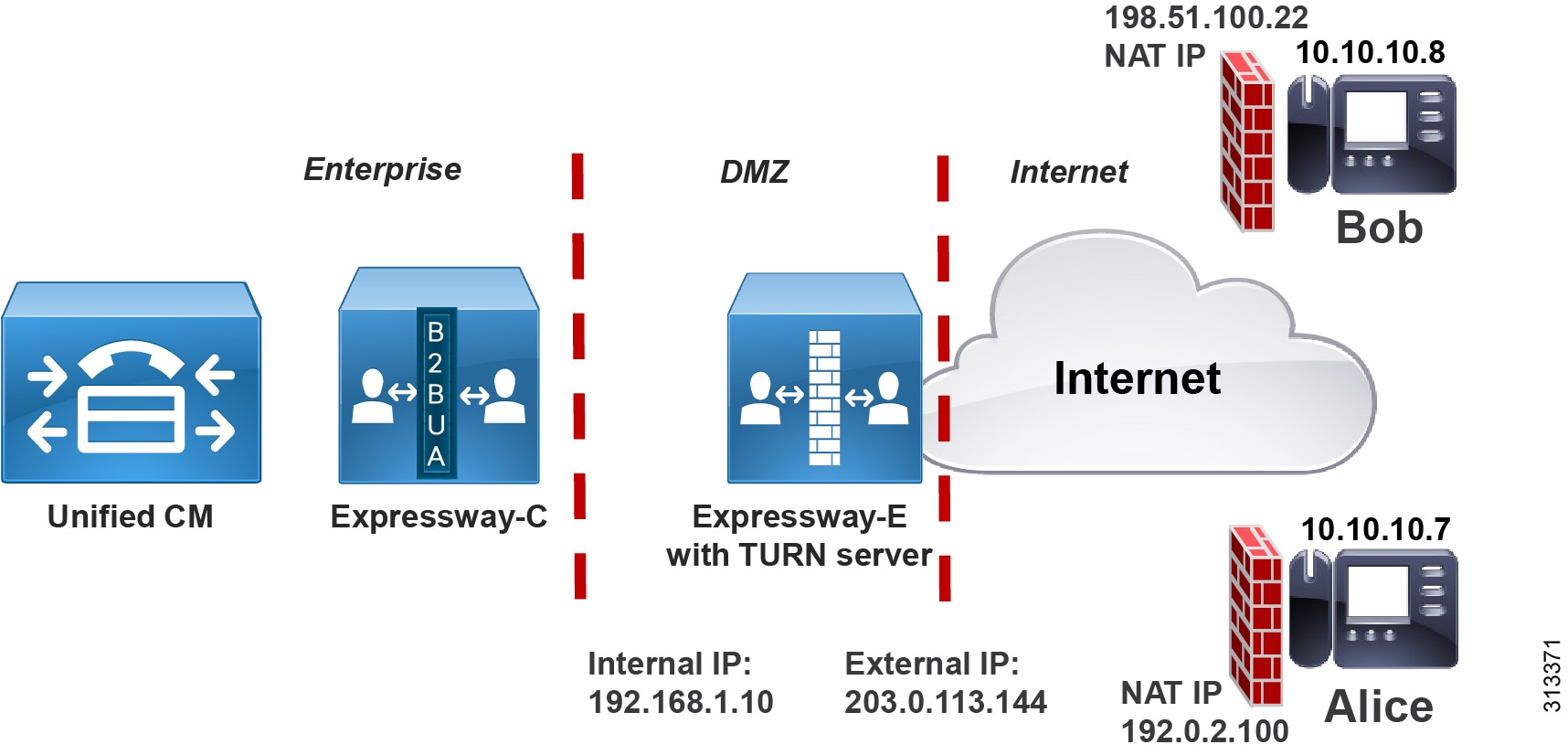
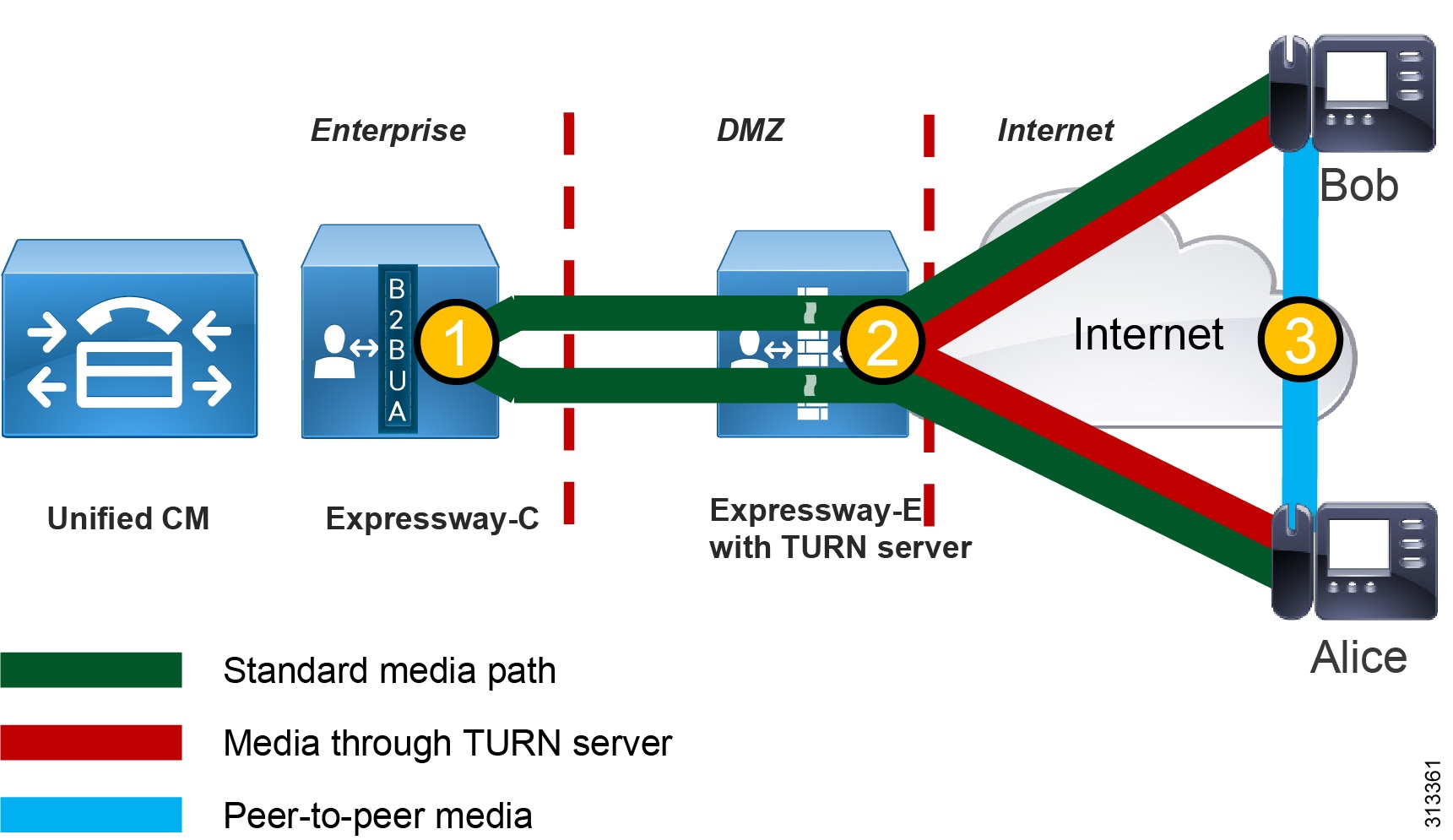
Media Optimization with ICE Enablement in Cisco Enterprise Collaboration Preferred Architecture 12.5 - Cisco
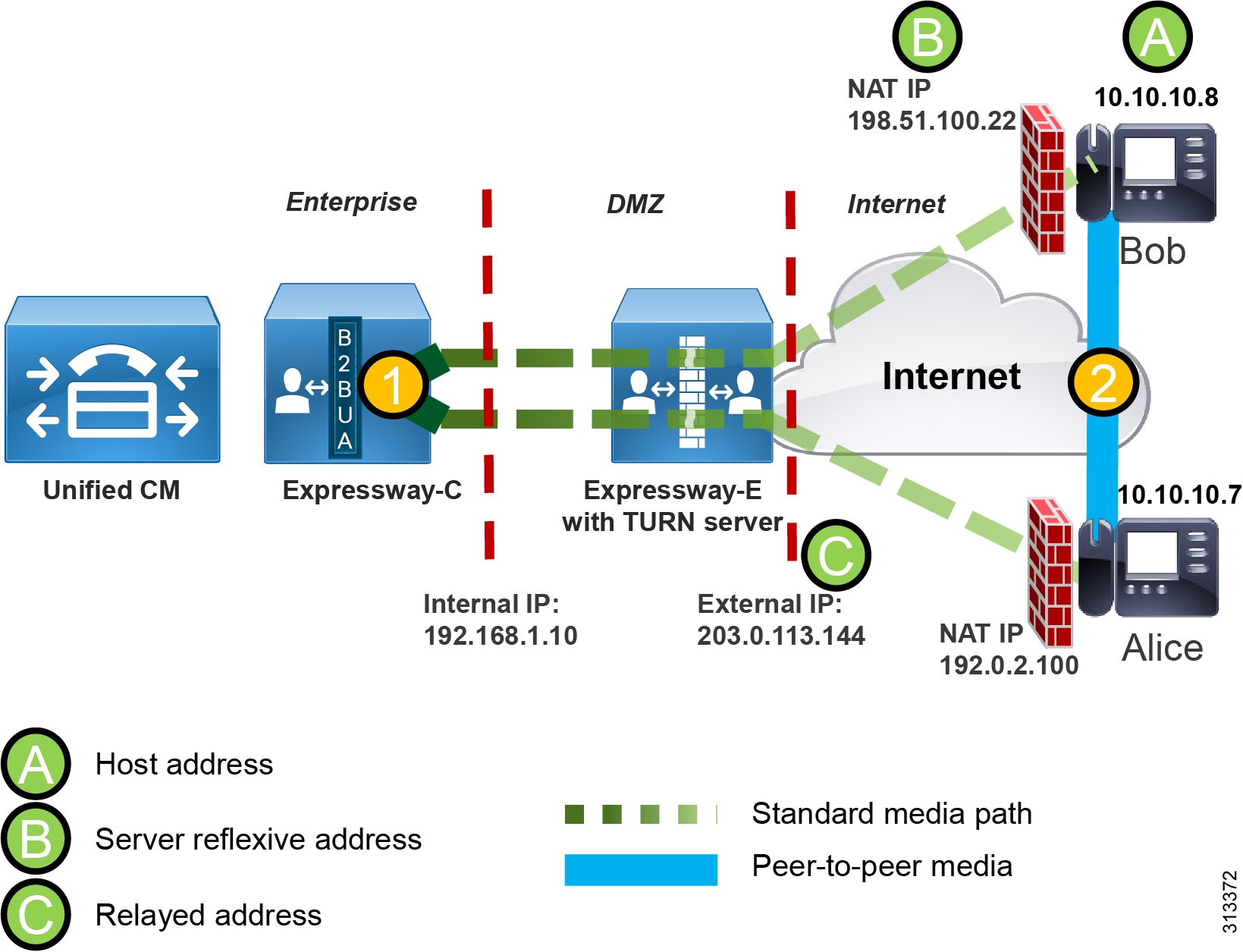
Media Optimization with ICE Enablement in Cisco Enterprise Collaboration Preferred Architecture 12.5 - Cisco
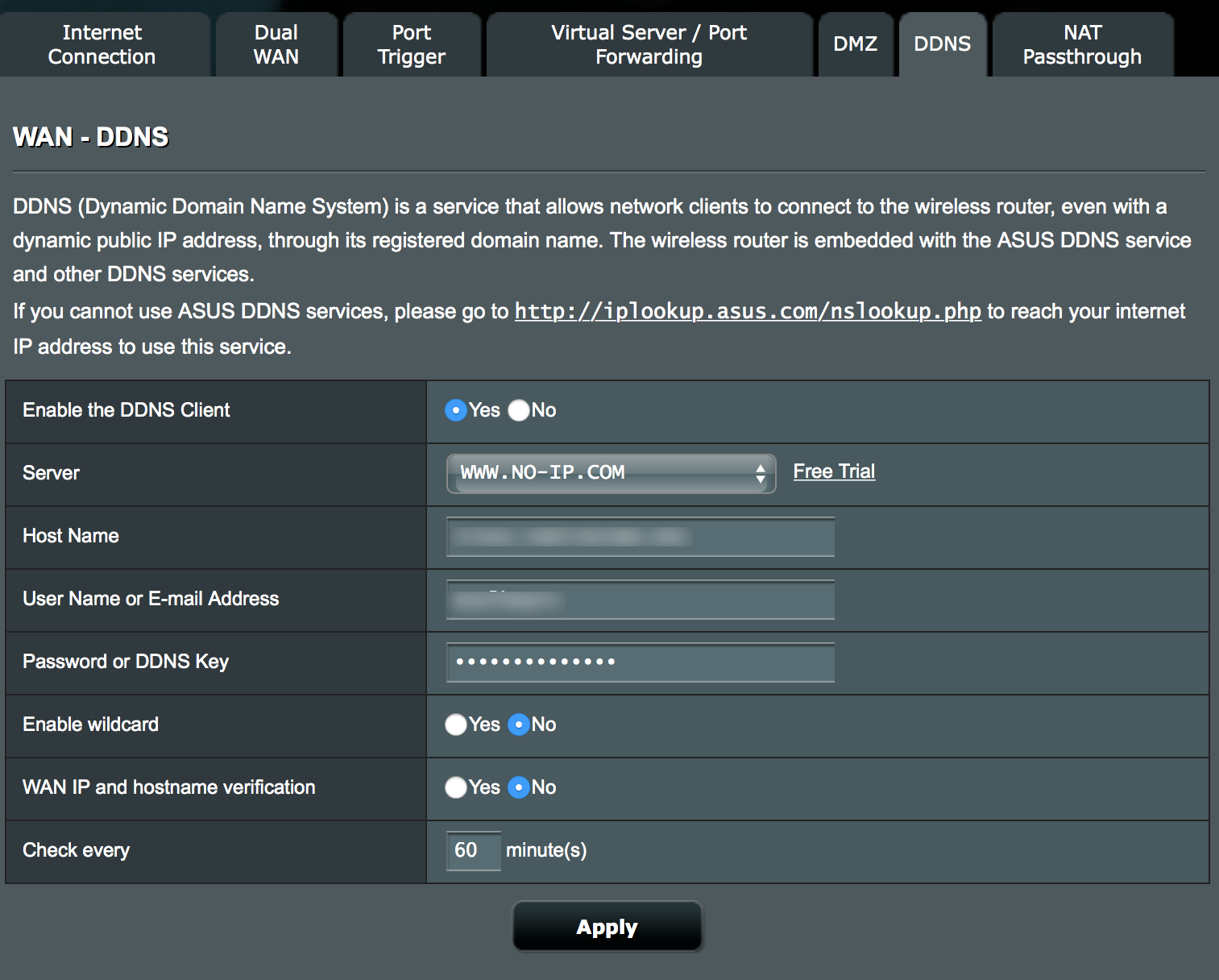
/cdn.vox-cdn.com/uploads/chorus_asset/file/13996416/2012_mpls_bypass.1419970333.png)